If you’ve ever evaluated software, you’ve likely seen vendors list security certifications like SOC 2, ISO 27001, or HIPAA compliance. But what do these badges actually mean, and why should they matter when you’re building custom software?
These certifications signal that an organization adheres to rigorous security and privacy best practices, validated by independent audits. It’s about how they safeguard data at every level, from infrastructure to internal workflows.
When you’re building custom software, the features you design today – access controls, audit logs, encryption – determine whether your system can adapt to compliance needs tomorrow. That’s especially true if you handle sensitive data (health records, financial info, or personal identifiers).
Below, we’ll cover the basics on what security frameworks are, what types of features help organizations comply with them, and some other best practices for putting security first.
What are security frameworks, and why do they matter for software development?
Security frameworks are blueprints for risk mitigation, defining the technical controls, documentation, and operational practices needed to protect data. This includes cybersecurity features built into software, but many security frameworks also address things like employee training, company policies, and physical security.
They fall into two categories:
- Legal requirements (for example, HIPAA in the US for healthcare, or GDPR for EU data).
- Voluntary certifications (for example, SOC 2 or ISO 27001) that require audits but aren’t mandated by law.
One caveat is that legal requirements will vary depending on where your users are. For global companies, voluntary frameworks offer standards that can streamline compliance across regions, which explains their growing popularity for international businesses.
Below are some overviews of how popular voluntary and regulatory frameworks compare:
Even when they’re not legally binding, these frameworks act as critical trust signals. Enterprise clients often require certifications like ISO 27001, while smaller businesses see them as proof of commitment to security. The stakes are high: In 2024, the average cost of a data breach hit $4.88 million (IBM), making compliance a financial imperative.
However, compliance can be intimidating for businesses just starting out with refining cybersecurity practices. Fortunately, there are some simple ways your software can create a good foundation for compliance.
Building compliance into custom software
When you’re building custom software, think of compliance like car safety:
- Your software is like the car’s design – it needs built-in safeguards (encryption, access controls).
- Your business operations are like the traffic laws and driver – training, policies, and physical security keep the car moving safely.
Just as a well-designed car doesn’t guarantee safe driving, your software’s security features alone won’t guarantee compliance with security frameworks – but those features can make it a lot easier to follow operational guidelines and audit your organization.
A closer look
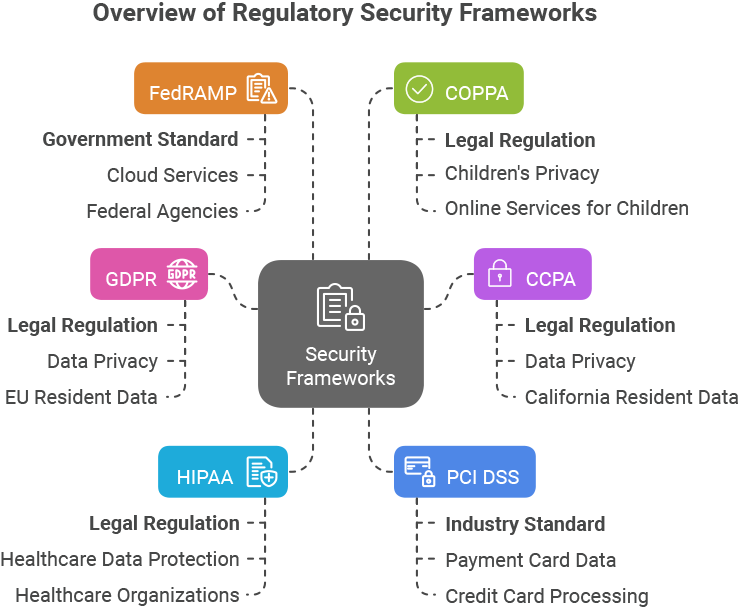
GDPR, CCPA, and COPPA protect data privacy
GDPR (General Data Protection Regulation), CCPA (California Consumer Privacy Act), and COPPA (Children’s Online Privacy Protection Act) are landmark privacy laws designed to give users control over their personal data.
While GDPR applies globally to any organization handling EU residents’ data, CCPA protects California residents and targets larger businesses. COPPA protects the data of children under 13 in the US. All of these frameworks focus on transparency and user control, but with different approaches.
Both GDPR and COPPA require explicit consent for data collection upfront, along with ways to track and delete stored personal data. In the case of GDPR, that means first-party consent and control – while COPPA places that authority with parents. CCPA, on the other hand, allows implied consent with opt-out rights for data sales.

Vertical Motion’s work with eTrove, a medical marketing platform, included features to help with both COPPA and HIPPA compliance. It offered referral programs for adult patients, with a system for kids to redeem points for gifts at their Orthodontist’s office for good dental care – requiring best practices for both privacy frameworks.
Software features that align with these frameworks include:
- Privacy dashboards for users to manage consent (GDPR and COPPA) or opt out of data sales (CCPA).
- Automated tools to handle data access/deletion requests within legal deadlines (e.g., 30 days under GDPR).
- Data mapping to track where personal information is stored and streamline compliance audits.
- Age verification mechanisms to trigger parental consent flows (COPPA).
Last year, OpenAI was fined over $15 million for using personal data to train chatbots without explicit consent. Recently, the company has been in the news with another GDPR-related complaint: hallucinations which produce inaccurate information about individuals. It’s a good reminder that caution is the best approach when handling user data, especially in the EU.
HIPAA, PCI DSS outline industry-specific approaches
Some security frameworks apply to specific industries handling sensitive data. HIPAA (Health Insurance Portability and Accountability Act) regulates protected health information (PHI) in healthcare, while PCI DSS (Payment Card Industry Data Security Standard) governs organizations processing credit card transactions.
HIPAA security frameworks protect any health or medical data that can identify someone, including things like patient records and billing information (also known as personal health information, or PHI). If the data reveals both someone’s health status and identity, it’s protected under HIPAA.
PCI DSS helps prevent fraud by safeguarding sensitive payment information. Protected data falls into two categories: cardholder data (which must be encrypted) and sensitive authentication data (which can never be stored after authorization). The latter includes things like security codes on credit cards and PIN numbers.
Software features that help include:
- For HIPAA: Secure messaging platforms, audit trails for PHI access, and automatic logout for inactive sessions.
- For PCI DSS: Tokenization (to replace card numbers), fraud detection systems, and strict access controls for payment processing.
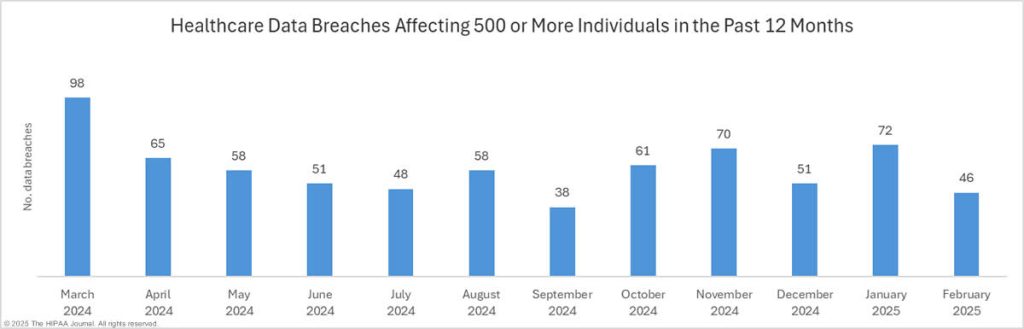
HIPAA Journal, Data Breach Report
It’s worth noting that some of the biggest recent healthcare data breaches are primarily from hacking and ransomware attacks. HIPAA imposes penalties after breaches occur, but doesn’t require frequent risk assessments – underscoring the need for broader security measures in addition to HIPAA guidelines.
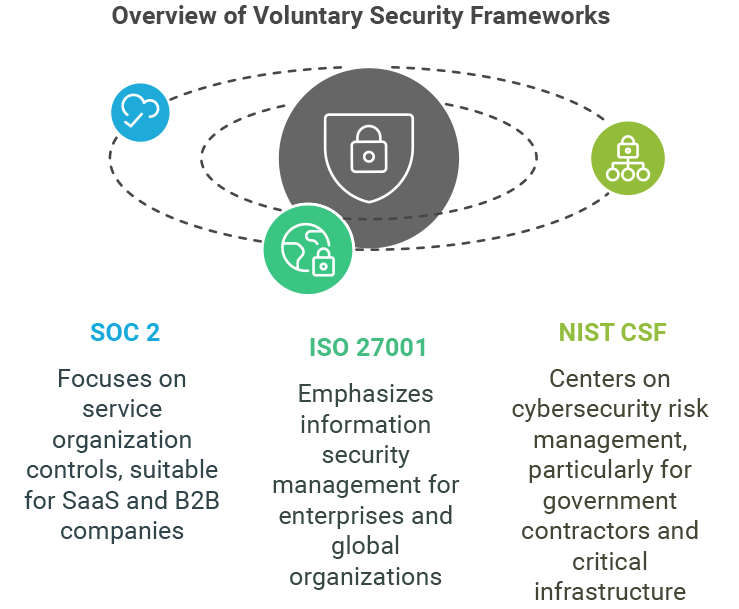
SOC 2, ISO 27001 include broad best practices for general security
SOC 2 and ISO 27001 are both voluntary frameworks, but they make it easier to meet legal requirements like HIPAA, PCI DSS, or GDPR. Unlike laws that apply to a specific region or industry, these frameworks are globally recognized and adaptable to any sector.
ISO stands for International Organization for Standardization, and they create voluntary standards for a variety of industries. ISO 27001 focuses on information security, cybersecurity, and privacy. The goal is to create an information security management system that includes things like risk assessments, encryption, and formal supplier agreements.
SOC 2 stands for Systems and Organization Controls 2, developed by the Association of International Certified Professional Accountants. Its focus is more on operational controls that protect the integrity, privacy, and security of data. Reports come as Type I (point-in-time) or Type II (ongoing controls).
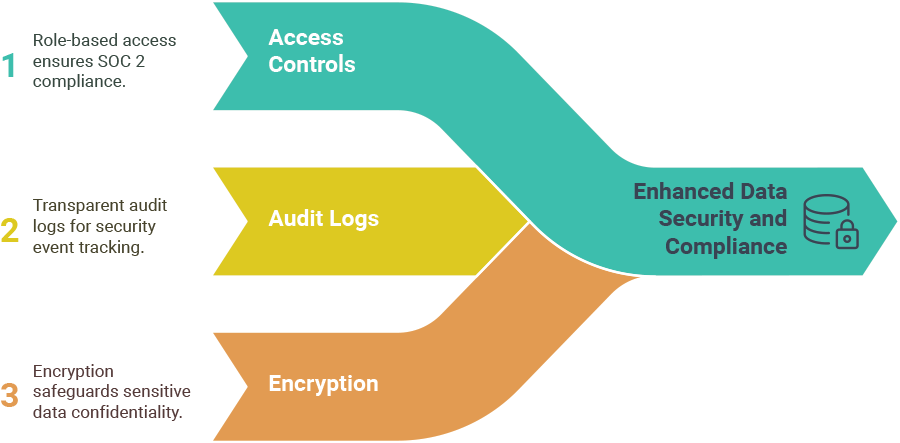
A few software features that can help achieve compliance with both are:
- Access controls including role-based access for SOC 2 and automated user provisioning for ISO 27001.
- Audit logs of security events for transparency on who did what, when, and how.
- Encryption to protect the confidentiality of sensitive data in transit and at rest.
However, security standards are more than just code: Verizon’s DBIR report found that 68% of breaches were due to human error. While features like encryption and access controls form the foundation, true compliance requires a security-first mindset that includes embedding security into every layer of your organization.
Other popular cybersecurity frameworks
The frameworks listed above are just a few of the most common frameworks – but there are many more. Others include:
- NIST Cybersecurity Framework, developed by the National Institute of Standards and Technology, which focuses on security governance.
- HITRUST CSF, which offers a single set of controls to comply with multiple frameworks, both legal and voluntary.
- CIS Controls, which focuses on streamlining operational controls, with less of a focus on risk assessment.
Best practices for a security-first mindset
Integrate security into the software development life cycle
The software development life cycle (SDLC) includes all the stages of development, including strategy, design, development, testing, deployment, and maintenance. This could include automated security scanning, threat modeling sessions at the beginning of new feature development, and regular code reviews focused on security vulnerabilities.

Conduct regular audits and assessments
Regular audits and assessments act as your “security health checks” to validate controls are working and uncover gaps in security before breaches happen. This might include things like checking access logs or scanning for vulnerabilities. Set clear timelines for fixing security issues and penetration testing, so security fixes don’t take a backseat to new feature development.
Collaborate with security experts
Build an incident response plan
Keep up with software maintenance
Left unmanaged, tech debt becomes security debt. Just as you’d patch a leaking roof, regularly maintaining software is crucial to managing tech debt that can impact security over time. Keeping dependencies, APIs, and documentation up to date can help prevent vulnerabilities from creeping in.
Sometimes, a security-first mindset starts with a closer look at your existing software. If that’s the case, our Application Health Assessment can help you know exactly where you stand, with recommendations for addressing security vulnerabilities.
Finally, it’s important to keep in mind that regulations and security standards change over time – so keeping up with new developments can help you stay compliant and safe.
Cybersecurity trends to watch
IBM predicts that this year, AI will have a big impact on security – for both defenders and attackers. AI-powered tools can help detect anomalies faster, automate incident response, and identify insider threats with behavioural analysis. But AI also introduces risks like:
- Shadow AI deployments that aren’t approved by the organization, risking data leaks
- LLM-powered social engineering for more realistic phishing attacks
- Lowered barriers to creating malware written by AI
AI’s rapid progress means that traditional security frameworks are struggling to keep up, particularly with consent issues around AI data use and explaining AI decision-making. Security frameworks will likely evolve to keep pace in the future.
Here’s the whole video for more on how AI will impact security:
As digital infrastructure gets more complex, attack surfaces will also grow and increase demands on security. SecurityWeek notes that rapid IoT adoption, cloud services, APIs, and new edge devices all create new security issues – and that a holistic approach is key to managing risk in these new environments.
Compliance is a competitive advantage
Security frameworks aren’t just about avoiding fines – they also build customer trust and organizational resilience. Whether you’re subject to GDPR, pursuing SOC 2, or safeguarding patient data under HIPAA, remember these basic principles:
- Design software with compliance in mind
- Operate with a security-first mindset
- Adapt continuously to new threats
At Vertical Motion, we can help create software that builds a foundation for secure operations. Want to learn more? Whether you’re interested in strengthening the security posture of your existing software or want to start from scratch, reach out to our team for a conversation.
Vertical Motion is a trusted Canadian software development and entrepreneur assistance company that has supported the global efforts of startups, non-profits, B2B, and B2C businesses since 2006. With headquarters in Calgary and Kelowna, and team members coast to coast, Vertical Motion is recognized as an award-winning leader in the technology industry. Our team of executive advisors, project managers, software developers, business analysts, marketing specialists, and graphic designers have extensive experience in several industries including — Energy, Finance, Blockchain, Real Estate, Health Care, Clean Technology, Clothing & Apparel, Sports & Recreation, Software as a Service (SaaS), and Augmented & Virtual Reality (AR/VR).
Come chat with us and let us take you “From Idea to Execution and Beyond!” 🚀